[clear type=”clear”]
You’re not anonymous online. Every move you make on the internet can be traced back to you, using your IP address. It doesn’t matter if you’re visiting a secure and highly encrypted website. The websites always know who you are! No wonder some European countries consider IP addresses as personally identifiable information.
But what if you don’t snoopy people tracing you? What if you want to be really anonymous? We’re here to help. In the following tutorials, we will teach you how to protect your privacy online with the Tor Browser.
The Internet was never designed to be an anonymous platform. Never. Take this for an example :
[clear type=”clear”]
[quote_center]
[clear type=”clear”]
As you can see above, it’s very easy to know about you just from your machine’s IP address. Click here to see the whole list of information. You’ll be amazed what all the websites know about you! Now think about all your personal information changing hands, so easily. Scared?
[clear type=”clear”][quote_center]Okay Now Relax.[/quote_center][clear type=”clear”]
We have something that might help. A tool to keep you anonymous.
Welcome to the world of Tor : Where you can browse in secret
Tor was developed in 2002 by the US Navy for protecting government communications. It was soon adopted by techies across the world. The Tor software protects you by bouncing your communications around a distributed network of relays run by volunteers all around the world: it prevents somebody watching your Internet connection from learning what sites you visit, it prevents the sites you visit from learning your physical location, and it lets you access sites which are blocked. Basically, it keeps you anonymous.
For the more technically minded folks:
[quote_simple]Tor is an encrypted network that can route your traffic through relays, making the traffic appear to come from exit nodes. Unlike with proxies, the exit node itself doesn’t know your IP address or where you are.[/quote_simple]
How Tor Works
Unless you really are interested in the dynamics of Tor and can handle complicated technical jargon, I suggest you skip this section and move on to what matters to you most – how to get Tor.
The data being transmitted from your PC is en-capsuled by multiple ‘layers’ of encryption. This encrypted capsule is then transmitted to the Entry node of the Tor Network. At every step of this circuit, one layer of encryption is removed thus revealing the next relay in the circuit. Each relay along the way knows only which relay gave it data and which relay it is giving data to. No individual relay ever knows the complete path that a data packet has taken.Thus, your data is relayed anonymously to the destination website. This prevents the website from having access to personal identifying information.
For a more detailed explanation I recommend you read Tor Project’s website.
Tor Bundle
The Tor browser comes as part of the Tor Bundle – a complete package which allows you to connect to the Tor network without any installation on Windows, Mac OS X, or Linux. It comes with a pre-configured web browser to protect your anonymity.
Getting Started with Tor Browser
You can easily download the Tor Browser Bundle from here.
Now you need to extract the 7-Zip self-extracting archive into the folder where you want Tor to operate from. This can be anywhere, of course.
Now that you’ve successfully extracted the Browser Bundle, give it a whirl. Go to the extracted folder and double click on the file “Start Tor Browser.exe”.
You need to wait now! You’ll be seeing the Vidalia Control Panel on your screen. Vidalia is a cross-platform controller for the Tor software. This piece of software is responsible for creating the global relay circuit and to connect you to the Tor network. It also lets you configure your Tor client, bridge, or relay with a simple interface.
Once the connection to the Tor network has been made, the Tor Browser will be launched.
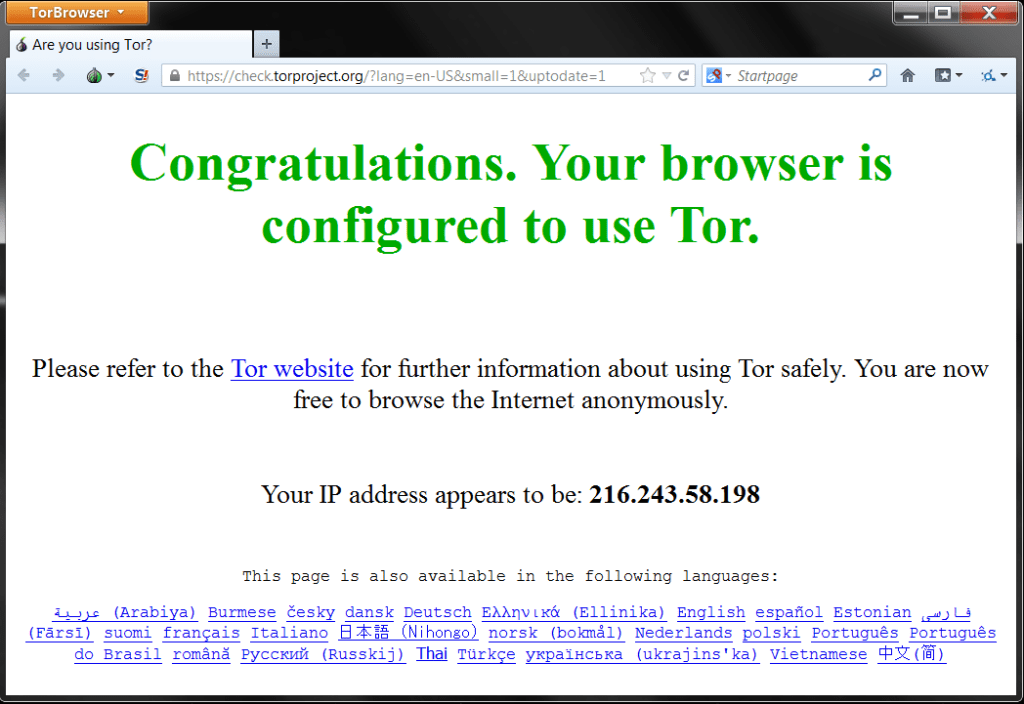
You’re now connected to the Tor network! This window is considered to be an ungovernable space where web users can surf with complete anonymity. As long as all your surfing is done from here, your identity online is protected.
As you can see below,
The Tor browser is configured to go through 127.0.0.1 i.e your local proxy. This local proxy is setup by Vidalia for connecting to the Tor network. You may note that other applications can also be configured to use the Tor network.
Now just to be sure if you’re browsing the internet anonymously, do a simple IP lookup.
Do’s and Don’ts
[check_list]
- If you need to be anonymous (whatever be your reasons), use Tor Browser only – It’s pre-configured to protect your privacy and identity online. Any other browser might be unsafe.
- Use HTTPS versions of websites only
[/check_list]
[delete_list]
- Don’t open documents downloaded through Tor while online.
- Don’t provide any personal information online. For eg. Never Login into account associated to you like Facebook etc.
[/delete_list]
Tor is for Mobile too
[appbox googleplay org.torproject.android]
[appbox appstore 519296448]
That’s it then. Have fun browsing anonymously !