A Statista report predicts that data generation will hit an astonishing ~180 zettabytes by 2025 – an increase of 118.8 zettabytes compared to 2020. As the quantity of data we generate grows exponentially, the requirements for data storage also surge significantly. And it’s edge computing we will rely on for meeting these requirements.
Edge computing refers to a decentralized information technology (IT) framework where data from clients is handled at the network’s outer edges, as close as feasible to its point of origin.
Edge computing involves processing, analyzing, and storing data in proximity to its source, facilitating quick and nearly instantaneous analysis and reactions. In recent times, a few businesses have opted to streamline their activities by concentrating or centralizing data processing and storage in cloud-based systems.
However, the requirements posed by emerging scenarios made possible by countless interconnected devices, spanning from cutting-edge warehouse management and inventory solutions to vision-boosted robotic production lines and sophisticated smart city traffic management systems, have rendered this approach unviable. This creates the need for a distributed computing paradigm that brings computation and data storage closer to the source of data generation, enabling real-time processing and analysis.
Core Principles
Some of the core principles of edge computing are as follows:
- Proximity: Processing data in close proximity to its origin, this novel technology reduces latency and minimizes the necessity for data to travel extended distances to access a centralized data facility.
- Bandwidth Efficiency: By processing and sieving data at the edge, only pertinent data is sent to the cloud or data center, enhancing bandwidth utilization.
- Immediate Responsiveness: This new technology endeavors to process data in the nearest feasible location to its source, making it optimal for applications demanding low latency and situations necessitating real-time decision-making.
- Offline Functionality: Edge devices can work independently even without network connectivity, ensuring uninterrupted operation in remote or isolated environments.
Exploring the Benefits of Edge Computing Applications
Edge computing has gained traction as a data processing alternative with several advantages for enterprises. Once again – since it permits data processing to occur at the network’s periphery, it results in:
- Quicker reactions,
- Heightened security, and
- Expanded scalability.
Edge computing can also enhance the security of your data architecture and software applications. With sensitive information closer to its source, it’s possible to distance data from vulnerable central servers and minimize data transmission over external networks. Thus, the likelihood of malicious interception is minimized. This is particularly significant in industries where security is critical, such as financial services or healthcare.
One of the biggest benefits of the emerging computing paradigm is that it minimizes latency by eradicating the need to shuttle data between a central server and distant devices. Through local data processing, response time is reduced. This proves advantageous for real-time applications demanding instant feedback, like self-driving cars and intelligent home setups. Edge Computing thus significantly impacts safety, effectiveness, and customer satisfaction.
Ultimately, the new technology has the potential to enhance scalability.
And it offers this by distributing computational resources across edge devices.
This allows organizations to handle increasing data volumes and processing requirements without overburdening centralized cloud infrastructures. Moreover, this strategy is cost-effective in situations where relaying substantial data volumes to the cloud would lead to elevated network expenditures. Edge computing offers bandwidth optimization, thus reducing operational costs. Consequently, organizations can:
- Cut down data transmission expenses,
- Enhance resource utilization, and
- Establish a more economically viable infrastructure by conducting localized data processing at the edge.
Such an approach is valuable for applications that might confront abrupt surges in utilization, such as streaming platforms. Netflix does exactly this with its CDNs!
Edge computing applications are efficient because only relevant and actionable information is transmitted. This helps in optimizing bandwidth usage, reducing network congestion, and improving overall efficiency.
Let’s now take a look at some real-world edge computing examples.
Real-World Edge Computing Applications
There are a multitude of real-world edge computing applications that operate beyond traditional data center settings. It finds utility in various contexts, such as smart cities, industrial IoT, automotive, retail, and healthcare.
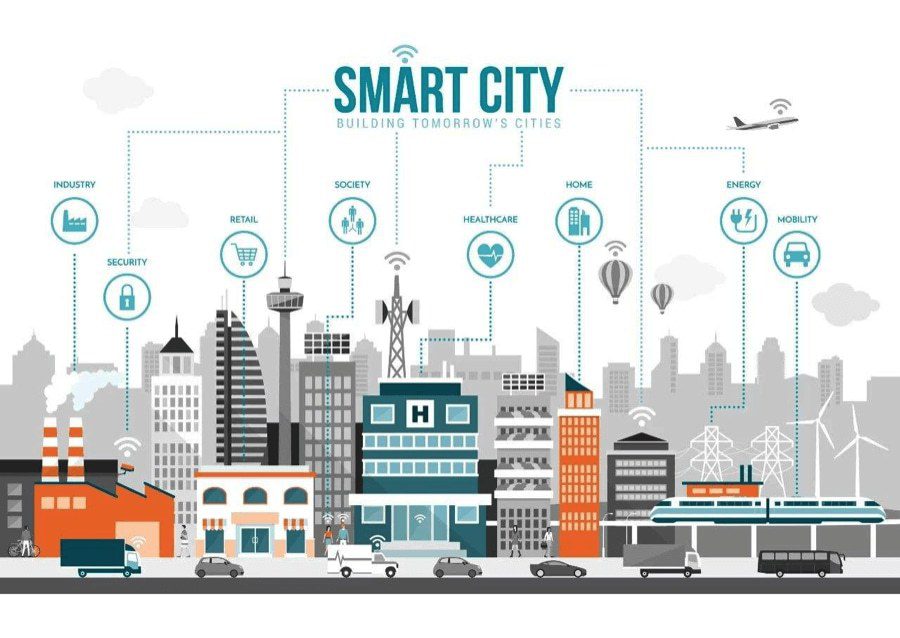
In the realm of smart cities, this technology holds a crucial position within initiatives where multiple sensors and devices gather data from diverse origins like traffic signals, surveillance cameras, and environmental sensors. Processing this data at the edge, urban centers can rapidly react to real-time occurrences, fine-tune traffic patterns, and heighten public safety measures.
Read more: Smart Cities and IoT: Opportunities Galore in India
In the case of edge computing examples like the retail industry and customer experience, the novel technology enables immediate customization and focused advertising. Within a retail store, edge devices can gather and assess customer data, providing targeted or customized suggestions and offers based on the customers’ preferences and behaviors.
One of the most significant and impactful edge computing applications is healthcare. Here, Edge Computing:
- Enables remote patient monitoring and treatment, along with real-time analysis of patient data, and
- Alleviates pressure on network infrastructure by locally processing crucial health information, resulting in faster diagnosis and intervention.
Some of the other popular edge computing examples are in the automotive sector and in industrial IoT. It is transforming industrial processes by facilitating instant monitoring and control of machinery.
In manufacturing plants, edge devices analyze sensor data to identify anomalies, forecast maintenance requirements, and enhance production efficiency.
One of the interesting real-world edge computing examples is in the education sector. Certain education software solutions employ on-device AI to provide:
- Individualized virtual support,
- Natural language interaction, and
- Augmented reality encounters.
For instance, ViewSonic’s whiteboard employs edge and vision technology to replicate traditional classroom interactions for remote learning.
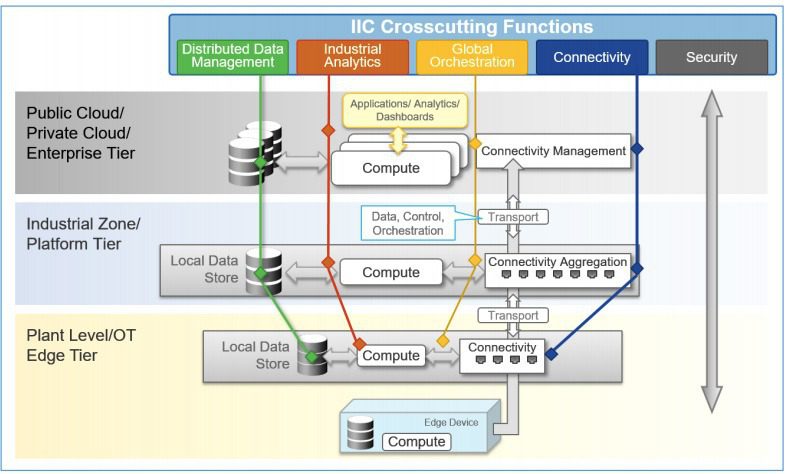
Smart grids, predictive maintenance, in-patient monitoring are only a few examples of how edge computing is revolutionizing data processing and storage.
How to Start Building Your Own Edge Computing Applications
To effectively implement this technology, organizations should follow these broad 6 steps:
- Identify suitable use cases for edge computing, prioritizing real-time processing and reduced latency, especially for applications like media streaming, autonomous vehicles, and IoT devices.
- Evaluate current infrastructure to identify gaps in hardware, software, and networking capabilities that may need enhancement to support edge computing.
- Choose an appropriate edge computing platform after careful assessment of options, considering scalability, security, and cost factors.
- Develop a comprehensive deployment plan outlining hardware, software needs, deployment timeline, and testing and validation procedures.
- Assess the impact on existing systems and processes, including data storage, access control, and security, to ensure a smooth integration of edge computing solutions.
This technology represents a paradigm shift in data processing and analysis by bringing computation closer to the network’s edge. However, like every other technology, it also has some risks. Although the new computing paradigm is gaining popularity for enhancing network performance and reducing latency, it introduces security challenges.
- A primary concern is safeguarding data on remote edge devices, which lack comparable security to those on secure corporate networks.
- Unauthorized access threats are heightened due to these devices’ distributed locations.
- Identity and access management complexities arise, as edge devices often have limited access to corporate resources.
- Compliance and regulatory issues emerge, necessitating awareness of relevant laws and regulations.
Organizations must address these challenges through proper security measures and legal adherence to ensure a secure and compliant edge computing environment. Thus, due diligence must be performed and protocols should be put in place for cases of emergency or security breaches, before adopting the novel computing technology in your organization.