Digital crimes are on the rise. And they can be devastating – financially and emotionally, for individuals and companies. Reports indicate a 15% surge in the global average cost of data breaches to USD 4.45 million in 2023. In such a scenario, a pivotal question arises: are traditional encryption methods, such as RSA and AES, robust enough in the face of escalating cyber threats? Well, the answer is no.
Traditional encryption to secure digital communications has served us well for many years. However, the increasing sophistication of cyber threats and the advent of quantum computing necessitate adopting more advanced security measures, such as quantum cryptography.
Traditional encryption is constrained by the necessity for a trusted third party to distribute cryptographic keys, introducing a potential vulnerability into the system. These methods, relying on mathematical algorithms, could be exploited by quantum computers.
To counter this, quantum cryptography emerges as a solution, leveraging the intriguing principles of quantum mechanics to offer unparalleled security.
Let’s first understand what quantum cryptography is:
What is Quantum Cryptography?
Quantum cryptography applies the principles of quantum mechanics to ensure secure communication between two parties. It relies on the fundamental properties of quantum particles to create a shared secret key between the sender and the receiver. This key is used for encryption and decryption.
The unique properties of quantum mechanics make it extremely difficult for eavesdroppers to intercept without detection.
As of 2023, there have been significant advancements in the field of quantum cryptography.
The scientific community is working towards cryptographic encryption that can withstand post-quantum threats. This is referred to as post-quantum cryptography (PQC). The point at which quantum computers will be capable of breaking existing cryptographic algorithms, called ‘Q-Day’, is near.
Key Principles of Quantum Cryptography

Let’s understand what are the principles driving the behavior of quantum cryptography:
Quantum Key Distribution (QKD)
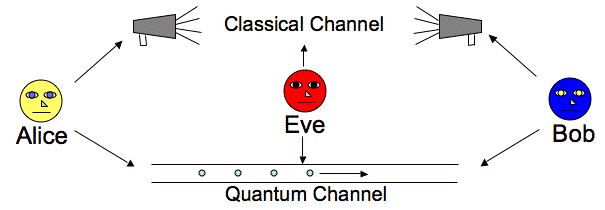
Quantum Key Distribution (QKD) is the foundation of quantum cryptography. It is the process through which two parties, let’s take them to be Alice (the sender) and Bob (the receiver), establish a shared secret key that is used for encryption and decryption. This key is generated using quantum particles, typically photons, to ensure a high level of security.
The steps involved in QKD include photon transmission, measurement, and key distillation. The QKD process guarantees that the shared key is known only to Alice and Bob, making it resistant to eavesdropping.
Heisenberg’s Uncertainty Principle
According to Heisenberg’s Uncertainty Principle, it’s impossible to know both the exact position and momentum of a particle simultaneously.
In quantum cryptography, this principle ensures that when an eavesdropper attempts to measure or intercept the quantum particles carrying the secret key, the act of measurement inherently disturbs the state of those particles. This disturbance is detectable, alerting Alice and Bob to the presence of an intruder.
Quantum Entanglement
Quantum entanglement is a phenomenon where pairs of quantum particles, such as photons, become correlated in such a way that their properties are interdependent, even when separated by vast distances.
Any change in the state of one particle instantaneously affects the other, no matter how far apart they are. Quantum entanglement is harnessed in quantum cryptography to detect eavesdropping attempts. If an eavesdropper attempts to intercept entangled particles, their actions will disrupt the delicate entanglement, triggering an alert.
No Cloning Theorem

The no cloning theorem in quantum mechanics asserts that it is impossible to create an exact copy of an arbitrary unknown quantum state.
This property is vital for the security of quantum keys. An eavesdropper cannot replicate the quantum key being transmitted, as doing so would violate the no cloning theorem. This inherent limitation ensures that quantum keys are resistant to duplication by potential attackers.
Now let’s see how these principles are brought to life by looking at a quantum cryptography example:
Quantum Cryptography Example
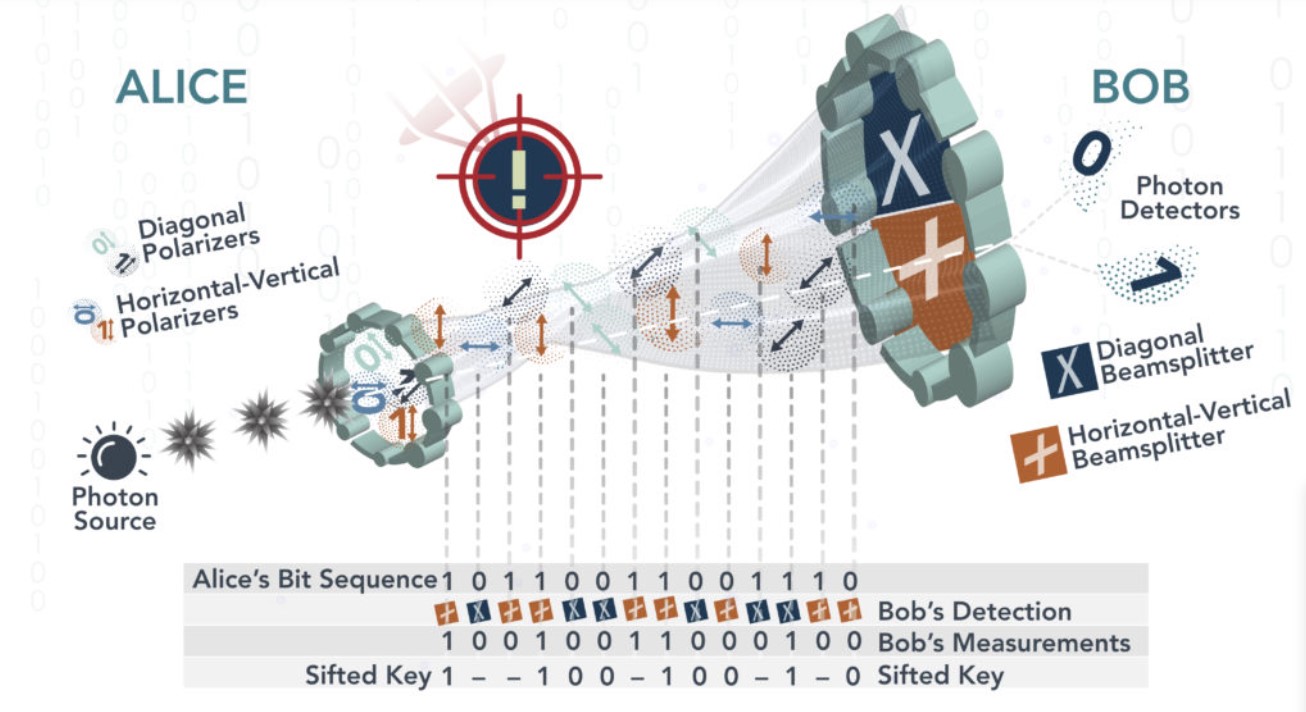
One of the most well-known quantum cryptography examples of the QKD protocol is the BB84 protocol, developed by Charles Bennett and Gilles Brassard in 1984.
Here’s how the BB84 QKD protocol works:
There are three participants:
- Alice: The sender of the encrypted message.
- Bob: The intended receiver of the encrypted message.
- Eve: A potential eavesdropper who may try to intercept the communication.
Key steps in the BB84 QKD Protocol:
- Photon preparation:
Alice generates a random sequence of bits (0s and 1s) and associates each bit with a basis (e.g., horizontal or vertical polarization for photons).
She then prepares a stream of photons according to these bit-basis pairs. If the bit is 0, the photon’s polarization is set according to the chosen basis. If the bit is 1, the polarization is set in the other basis.
- Quantum transmission:
Alice sends the stream of polarized photons to Bob, who awaits their arrival.
- Measurement by bob:
Bob also randomly selects a basis (horizontal or vertical polarization) for each incoming photon and measures its polarization accordingly. Bob records his measurement outcomes.
- Communication of basis information:
Alice and Bob now communicate with each other over a public channel (typically using classical encryption) to disclose the bases they used for measurement but not the measurement outcomes. This is called the basis reconciliation step.
- Basis matching:
Alice and Bob retain the measurement outcomes only when they use the same basis for a given photon. If their bases differed, they discard the measurement outcomes for that photon. This step ensures that they have a shared set of measurement outcomes for a subset of the photons.
- Quantum bit extraction:
After basis matching, Alice and Bob are left with a subset of photons for which they know they used the same basis.
They randomly select a portion of these matching measurement outcomes, and those selected bits become their shared secret key. These bits are used for encryption and decryption.
- Security verification:
To ensure the security of their key, Alice and Bob perform a security check. They exchange a small portion of their key to test for any discrepancies that may indicate eavesdropping.
If the test indicates that their key is compromised, they discard it and abort the communication.
How quantum cryptography works in this example?
- The security of the BB84 QKD protocol is based on the fundamental principles of quantum mechanics. When Eve tries to intercept the quantum bits transmitted between Alice and Bob, her measurements invariably disturb the quantum states of the photons, introducing errors into the measurement outcomes.
- Alice and Bob’s basis reconciliation step helps them detect inconsistencies in their measurement outcomes, which may indicate eavesdropping attempts by Eve.
- The key takeaway is that any attempt by Eve to intercept the quantum bits is detectable, providing a high level of security. This is what makes quantum cryptography, and the BB84 QKD protocol in this example, so secure.
This quantum cryptography example illustrates the core principles of quantum cryptography, particularly how quantum properties such as superposition and the no cloning theorem are harnessed to create an unbreakable encryption method.
Advantages of Quantum Cryptography
Quantum computing has diverse applications and has helped identify potential security breaches. Here are some other advantages of quantum cryptography:
- Unbreakable security: One of the primary quantum cryptography advantages is the security it offers which makes it extremely difficult for eavesdropping attempts to go undetected.
- Detects eavesdropping: Quantum cryptography offers an inherent ability to detect eavesdropping. Any attempt to intercept quantum particles carrying the secret key will inevitably alter the quantum states of those particles. This disturbance is instantly detectable, allowing the legitimate parties to halt the communication and investigate potential security breaches.
- Robust key generation: Quantum key distribution is a robust way to generate and distribute cryptographic keys. The QKD process ensures that the shared keys are known only to the communicating parties, reducing the risk of key compromise.
Disadvantages of Quantum Cryptography
Despite offering several advantages, quantum cryptography has its defects. Let’s look at some disadvantages of quantum cryptography:
- Cost and complexity: Quantum cryptography infrastructure can be expensive and complex to implement. Specialized equipment, such as quantum key distribution devices, are required, and maintenance can be costly. This can limit the widespread adoption of quantum cryptography.
- Limited range: The range over which quantum keys can be distributed is limited by the properties of the quantum particles used. Practical implementations are restricted to short distances, making it challenging to create large-scale quantum communication networks.
- Susceptibility to environmental factors: QKD systems can be sensitive to temperature, electromagnetic interference, and optical losses. These factors can impact their reliability and performance.
- Challenges in key management: Safely storing and managing quantum keys can be complex, and there is a need for further research and development in this area.
- Emerging quantum threats: In theory, the advent of a large-scale, fault-tolerant quantum computer poses a potential threat to asymmetric cryptography, which is the foundation of contemporary public key cryptography.
Applications of Quantum Cryptography

There are various applications of quantum cryptography. Below, we provide more some of the key applications of quantum cryptography:
- Secure communication: Quantum cryptography applications are widely used in sectors where data confidentiality and integrity are of paramount importance, such as government agencies, military operations, financial institutions, and healthcare providers.
- Government and military use: QKD are also used in national security and military operations as they require the highest level of data protection. Quantum cryptography is instrumental in securing classified information, safeguarding critical infrastructure, and ensuring secure communication among government entities.
- Financial services: The financial sector relies on quantum cryptography applications to secure transactions, protect trade secrets, and safeguard sensitive customer information. This technology ensures the privacy and integrity of financial data.
- Healthcare and medical records: Quantum cryptography applications are employed to secure electronic medical records and protect sensitive medical data. It ensures that patient information remains private and secure during electronic data exchanges.
- Secure video conferencing: In the era of remote work and virtual meetings, the demand for secure video conferencing has surged. Quantum cryptography is used to enable secure video conferencing, guaranteeing the privacy of confidential discussions and video calls.
- Quantum Key Distribution networks: Researchers are actively working on developing quantum key distribution networks that connect multiple parties securely over long distances. These networks have the potential to revolutionize global communication by providing unbreakable encryption for various applications beyond simple point-to-point communication.
- Internet of Things (IoT) security: The widespread use of IoT devices in various sectors, including smart cities, healthcare, and industrial automation, necessitates robust security measures. Quantum cryptography applications are employed to ensure secure communication between IoT devices, protecting against unauthorized access and data breaches.
- Cloud-based services: Ensuring the safe transfer of data is becoming increasingly important as more information is stored and processed in the cloud. Quantum Key Distribution (QKD) leverages quantum mechanics to establish a shared, secret, and random bit sequence between systems, offering a robust foundation for secure information exchange. Moreover, quantum cryptography addresses the potential vulnerability of current encryption methods to quantum computers, positioning itself as a future-proof solution.
- Secure voting systems: Quantum cryptography can be used to create secure and verifiable electronic voting systems. It encrypts and secures votes using quantum principles, ensuring the integrity of the voting process and providing tamper-proof election results.
- Aerospace and satellite communication: Quantum cryptography is employed in the aerospace sector to secure communication between spacecraft, satellites, and ground stations. This is essential for transmitting sensitive data, commands, and telemetry securely.
These applications of quantum cryptography highlight the versatility and importance of quantum cryptography in ensuring the security and privacy of sensitive information in an increasingly interconnected world.
The Road Ahead
Quantum cryptography serves as a game-changer by exploiting the fundamental principles of quantum mechanics. It provides unassailable encryption, making it an essential tool for preserving the confidentiality and integrity of data in the digital age.
It is certain to play a pivotal role in fortifying data protection in an interconnected and increasingly vulnerable world. With applications spanning secure communication, quantum key distribution networks, and IoT security, quantum cryptography is poised to revolutionize the way we protect digital information, offering an unrivaled level of security.
For more tech and science-related information, subscribe to Yaabot.


